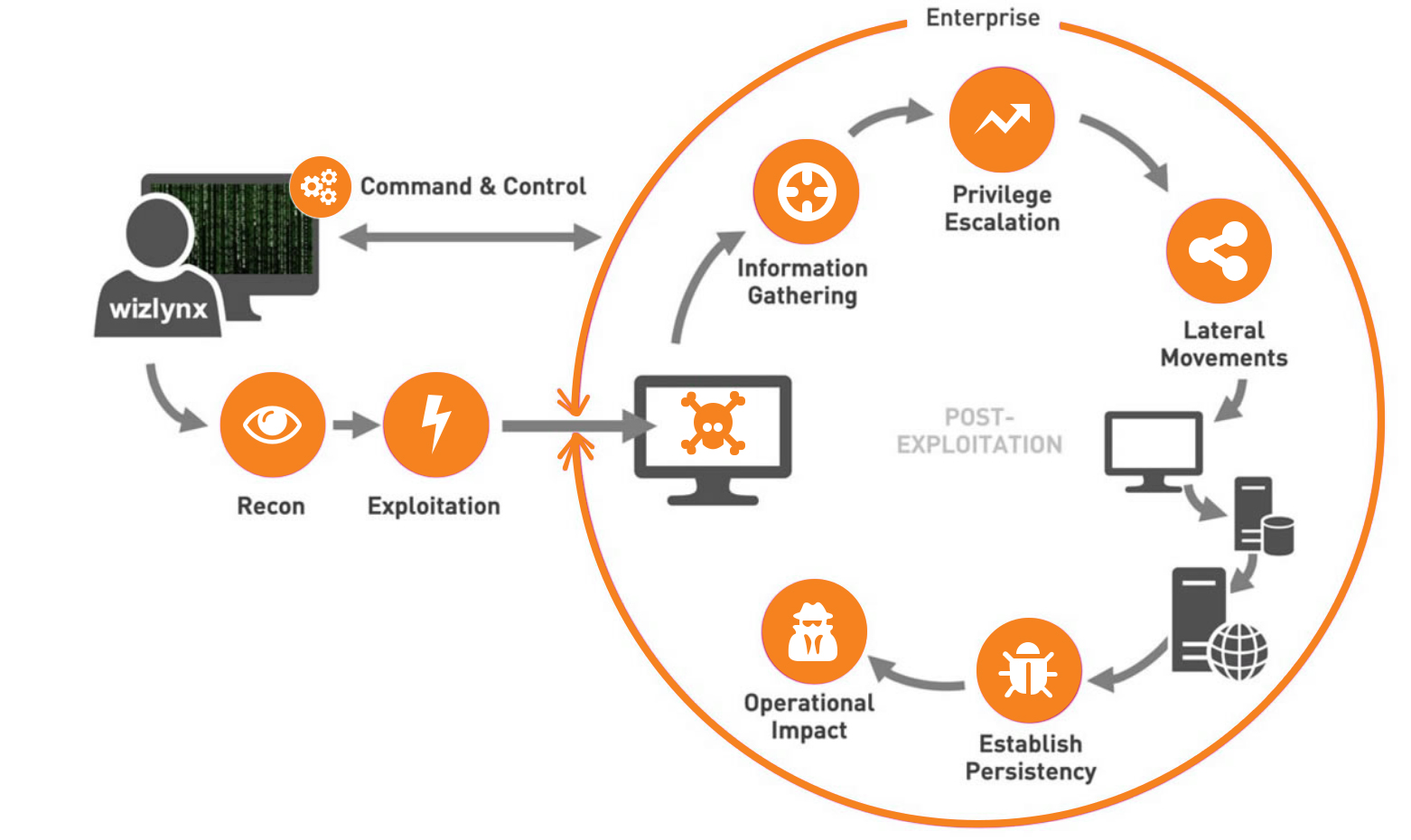
Network penetration testing makes use of several hacking techniques to find security holes in your networks. These tests employ real-world techniques and strategies that a malicious user could use to gain access to the network, thereby providing critical information about network security.
In a nutshell, network pen testing simulates a real-world attack, delivering important information about potential holes malicious threat actors could exploit to obtain access to your network(s).
The primary goal is to identify vulnerabilities in your computer systems that could allow unauthorised access or serve as an entry point into private regions of your network and sensitive data. This is accomplished through the use of vulnerability scanning technologies, the application of the most recent disclosures that may affect your systems and skilled manual penetration testing.
Secure your network by finding all the vulnerabilities present in the system. This ethical way of securing your network by finding the vulnerabilities not only safeguards your IT environment but also manages to find a brief about every loophole present on your platform.
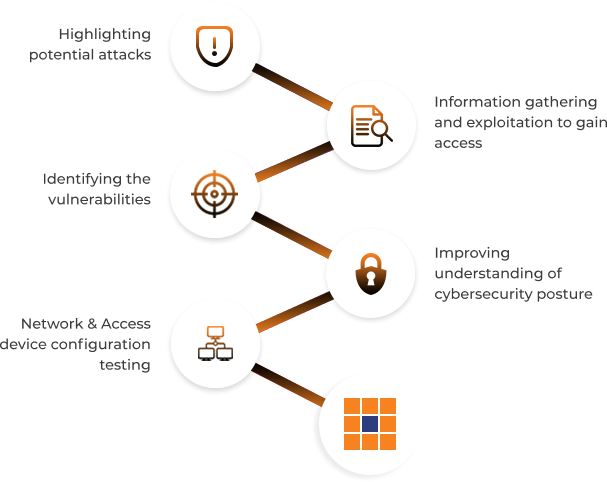
Your platform is a tempting target for hackers if it is not secured. Our penetration testing services will expose the vulnerabilities on your network and guide you to take adequate actions to prevent potential cyber-attacks and strengthen your defence.
Enhance your security and prevent possible threats that can gain unauthorised access to sensitive data on your platform. By collaborating with GoAllSecure to undertake a targeted Network Penetration Test, you will receive a stratified security approach tailored to your organisation’s specific environment..
You should get your business’s digital environment penetration tested at least once a year. You should also get a security check with the help of penetration testing when you are.

CASE STUDIES
Explore some of our projects showcasing our expertise in creating robust and scalable solutions.
Handling a Crypto Exchange Cyber Attack

A cryptocurrency exchange specializing in various digital currencies, including BTC and ETH, encountered a severe malicious attack. The attack created significant operational havoc, threatening the continuity of the business and risking catastrophic outcomes.

Our team responded promptly and with precision, conducting a meticulous investigation to identify the root cause of the attack. Immediate remedial measures were implemented to stabilize the situation. We then initiated a comprehensive cybersecurity management plan to safeguard the client's business against future threats, ensuring ongoing operational security and resilience.
Cybersecurity Management
Global
Securing a Fintech Web3 Platform

A client from the Fintech industry, focused on developing a web3 platform for cryptocurrencies, needed to address potential security gaps, particularly in platform security and user data privacy.

We identified and mitigated critical business logic vulnerabilities in the client's platform, preventing potential confidentiality breaches and revenue loss. By addressing these security concerns, we successfully met the organization's requirements.
Web Application Security Auditing, Network and Infrastructure Security, Cloud Security, API Security
OTHER TECHNOLOGIES WE WORK ON
Harness the power of our advanced technologies to elevate user interaction and drive engagement.
WHY CHOOSE US
We craft solutions that transform your business. Here's what sets us apart:

Competitive Rates
Our rates are highly competitive, ensuring that you receive excellent value for your money. With us, you can be confident that you are getting the best possible rates without compromising on quality.

Quality
We take pride in delivering exceptional results. Our CMMI level 3 appraisal and membership in the Agile Alliance demonstrate our commitment to strong processes and quality control. This ensures you get a polished, high-quality product every single time.

In-House Expertise
Our 1,000+ designers, developers, and project managers are all directly employed by us and work in our own offices across the US, UK, India, and globally. This ensures seamless collaboration and control over your project.

Security & Confidentiality
Unlike many offshore companies, security is our top priority. Your data and intellectual property remain completely confidential, and all source code rights belong to you, always.

On-Time Delivery
We use cutting-edge project management tools and agile development practices to keep your project on track. This means you'll get high-quality products delivered exactly when you expect them.

Flexible Engagement Models
We understand that your needs can change. That's why we offer flexible engagement options. Choose the model that works best for you now, and switch seamlessly if your needs evolve. We're committed to building a long-term, reliable partnership with you.
HIRE AS PER YOUR REQUIREMENT
At Dotsquares, we provide flexible options for accessing our developers' time, allowing you to choose the duration and frequency of their availability based on your specific requirements.


When you buy bucket hours, you purchase a set number of hours upfront.
It's a convenient and efficient way to manage your developer needs on your schedule.
Explore more



In dedicated hiring, the number of hours are not fixed like the bucket hours but instead, you are reserving the developer exclusively for your project.
Whether you need help for a short time or a longer period, our dedicated hiring option ensures your project gets the attention it deserves.
Explore more
OTHER TECHNOLOGIES WE WORK ON
Companies employ software developers from us because we have a proven track record of delivering high-quality projects on time.
WHO WE ARE
Companies employ software developers from us because we have a proven track record of delivering high-quality projects on time.









Testimonials
Be inspired by our clients' journeys as we overcome challenges and achieve success together.
Faq
We identify vulnerabilities such as open ports, misconfigurations, outdated software, and weak authentication protocols, providing insights into potential entry points for malicious actors.
Our testing is conducted carefully to avoid disruption, using controlled methods and schedules that ensure minimal impact on your business operations and network performance.
Yes, we provide a comprehensive report outlining all identified vulnerabilities, potential risks, and actionable recommendations to enhance your network's security posture.
The duration varies based on network size and complexity, but most tests range from a few days to a week. We provide a timeline after the initial consultation.
Yes, but testing during business hours may increase the risk of minor disruptions. We recommend scheduling during off-hours to minimize any potential impact on operations.
